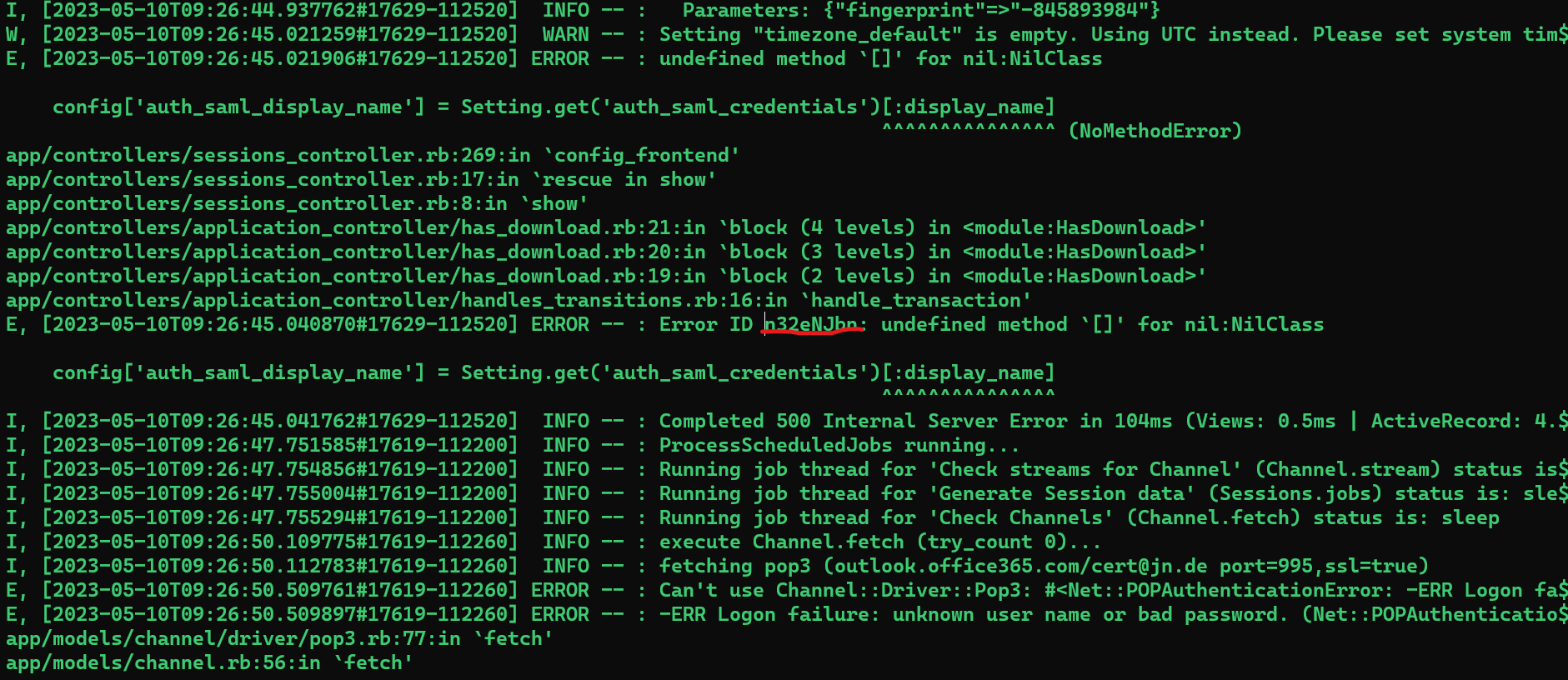
Yes, this is the main problem then.
The auth_saml_credentials setting was added around 4 years ago, seems to be that the setting was removed manually or the migration in the past didn’t work (when the system is already that old, otherwise the initial installation was not correct).
To fix this problem you could try this:
zammad run rails r "Setting.create_if_not_exists(
title: __('SAML App Credentials'),
name: 'auth_saml_credentials',
area: 'Security::ThirdPartyAuthentication::SAML',
description: __('Enables user authentication via SAML.'),
options: {
form: [
{
display: __('Display name'),
null: true,
name: 'display_name',
tag: 'input',
placeholder: __('SAML'),
},
{
display: __('IDP SSO target URL'),
null: true,
name: 'idp_sso_target_url',
tag: 'input',
placeholder: 'https://capriza.github.io/samling/samling.html',
},
{
display: __('IDP Single Logout target URL'),
null: true,
name: 'idp_slo_service_url',
tag: 'input',
placeholder: 'https://capriza.github.io/samling/slo.html',
},
{
display: __('IDP certificate'),
null: true,
name: 'idp_cert',
tag: 'textarea',
placeholder: '-----BEGIN CERTIFICATE-----\n...-----END CERTIFICATE-----',
},
{
display: __('IDP certificate fingerprint'),
null: true,
name: 'idp_cert_fingerprint',
tag: 'input',
placeholder: 'E7:91:B2:E1:...',
},
{
display: __('Name Identifier Format'),
null: true,
name: 'name_identifier_format',
tag: 'input',
placeholder: 'urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress',
},
{
display: __('UID Attribute Name'),
null: true,
name: 'uid_attribute',
tag: 'input',
placeholder: '',
help: __('Attribute that uniquely identifies the user. If unset, the name identifier returned by the IDP is used.')
},
{
display: __('Your callback URL'),
null: true,
name: 'callback_url',
tag: 'auth_provider',
provider: 'auth_saml',
},
],
},
state: {},
preferences: {
permission: ['admin.security'],
},
frontend: false
)"